Google dork list or Google dorks query are some set of codes and database injections that can be used to hack illegally and legally. A typical Google Docking can basically be used to make some advance searched, surfing the dark web or sniffing a website vulnerability including a database breach. Dorks can put all the sensitive information on the website in real peril.
Google dork list can put sensitive information at high risk as they unwittingly create back doors that allow an attacker to enter a network without permission and/or gain access to unauthorized information.
In short, Google dorks are a set of codes and SQL injections that hackers can use to access all information on a website by doing some advance search using these codes and injections. Accessing your website’s login page in an unauthentic way is a simple example of Google Dorks.
READ ALSO:
How does Google Dork Work
To know all about Google Dorks, I would like to take you back to the year 2002, the year when Serena Williams celebrates her victory ass she beats her older sister Venus 7-6, 6-3 for her first Wimbledon singles title in Wimbledon Women’s Tennis.
Meanwhile an employee at Google, Johnny Long was busy collecting some interesting Search queries that uncovered some vulnerable systems and/or sensitive information disclosures – labeling them google Dorks or Google Hacking.
Google dork provides a hacker or an advanced level user some special search method which is usually no open to anyone. A hacker uses Google search to inject some specific codes to access vulnerable data of a website to access their database or some private data that are not accessible through normal Google Search.
Hope I am clear to define the Term Google Dorks, You may use the comment box below if you find me wrong or you have any question.
Use Google Dorks to Hack
Now, I am going to show some examples to show you the complete Google Dorks in action, here I have collected a list of Google Dorks and injections which I will be using to display the Dorking in action.
Google Dorks Example
In this example, we shall try to download a music file sung by Eminem. A typical search format will look like this as shown in the example below.
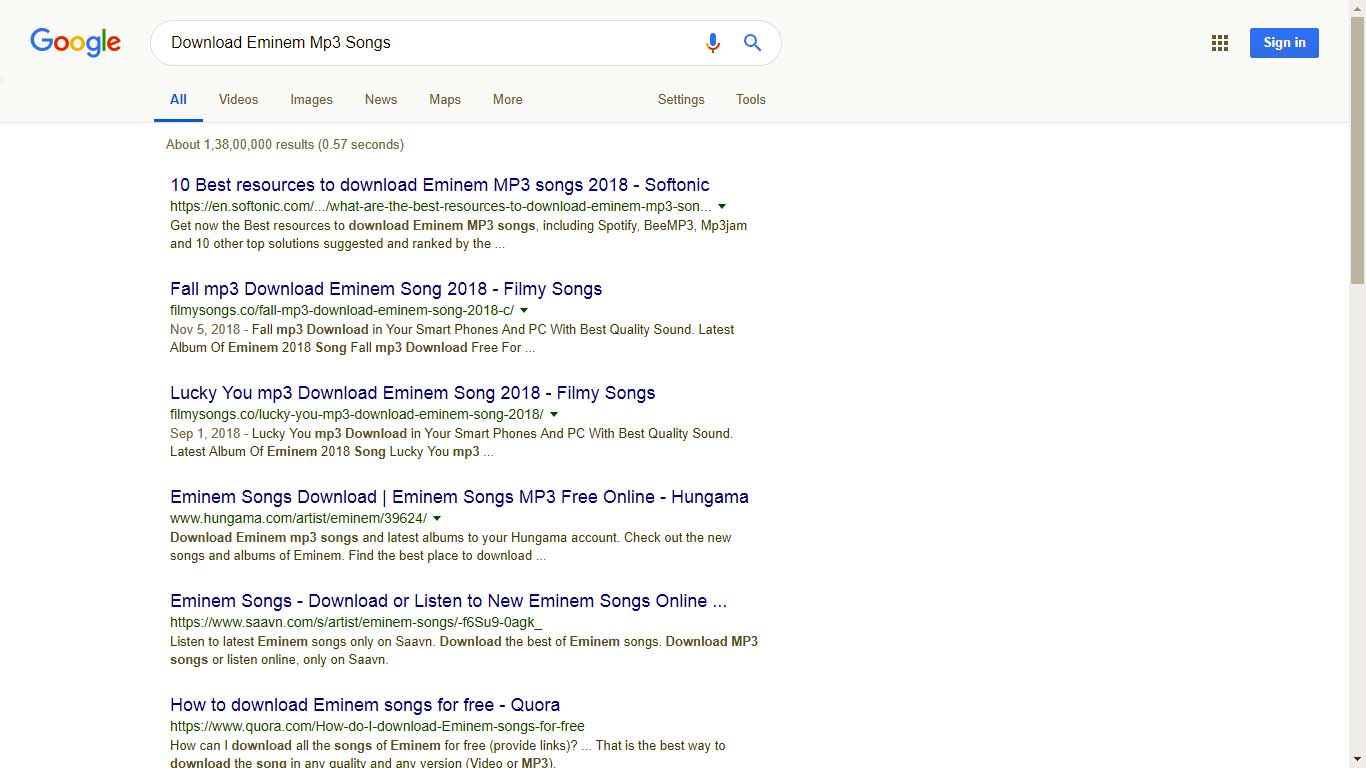
Download Eminem Mp3 Songs
By searching with this search term Google returns us a page full of link pointing to the websites which contain the song sung by Eminem, a list of site which allow to download the mp3 music by Eminem or it may contain some wiki pages and many more other pages which are related to Eminem(See Image Below)
Now we will try some Dorks to search the Music sung by Eminem and we shall directly hit to the database of the website, and download the music, without even opening the music website page. Here we need to inject some Dorks or queries to make it happen.
Index: of .mp3 Eminem
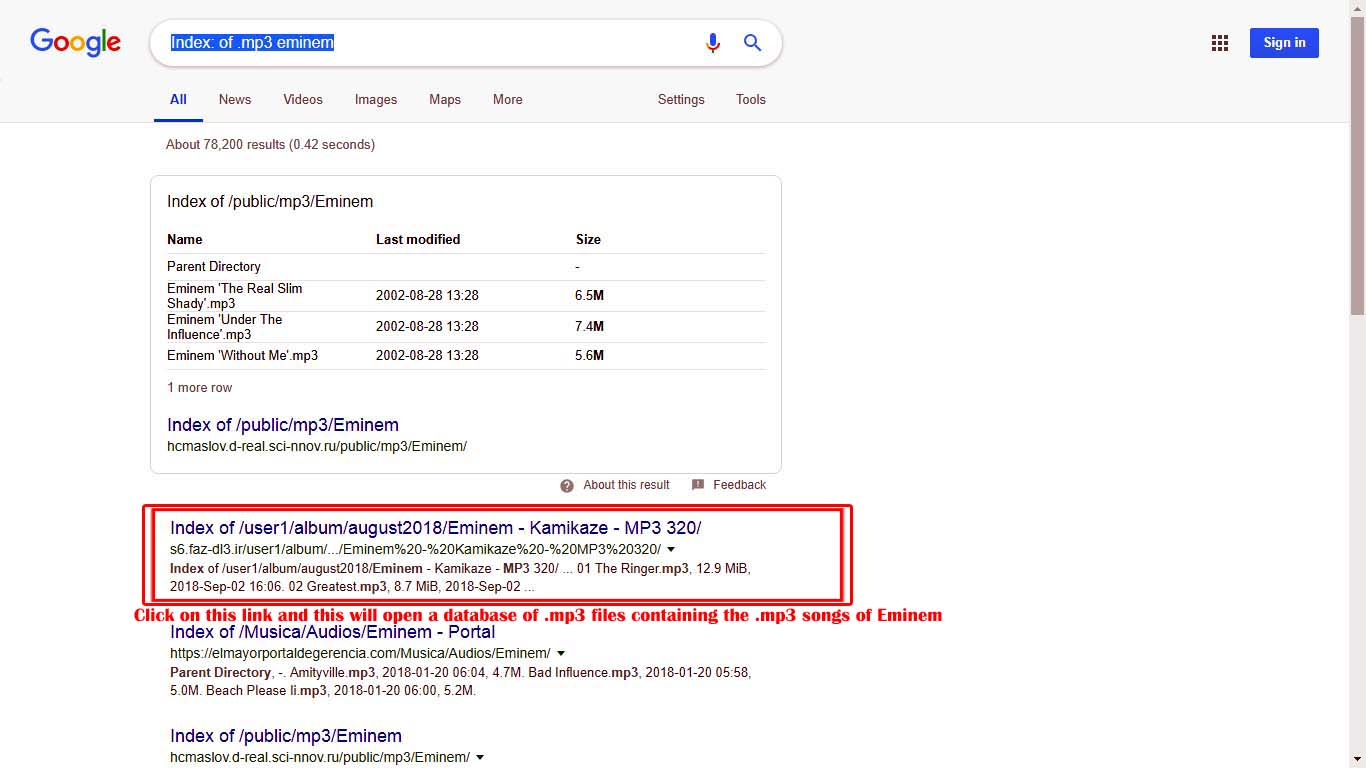
In the example above we have used injection “Index” which will display the list of all vulnerable website’s database link which contains any Mp3 file that contains the word “Eminem” in the name.
Once you click the link, you will be directed to the database page of the website and you can simply download the music by simply clicking the files displayed on the list. (see exactly example below)
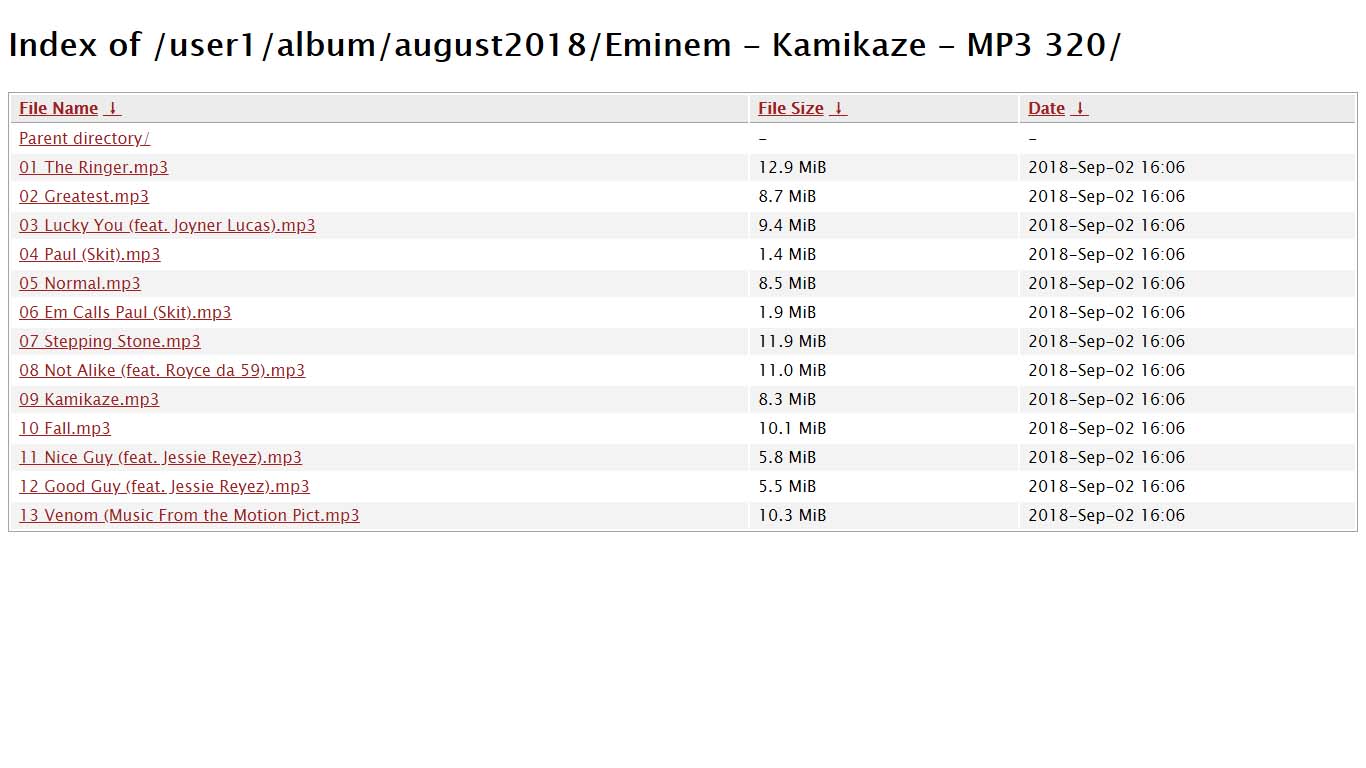
So here was a simple example of Google Dorks, Most people confuse it with Hacking, A hacking which can let them access all the Email ID, it’s password and all the personal stuffs like that.
You can search Google Dorks list on google and it will return you a hand full of Dorks. Enjoy!!
List of Google Dork database Injections
Here is the list of 2000+ Google Dorks which can be used for database injection. Though the use of Google dorks is illegal and against the law. You are advised to avoid using it.
RELATED:

